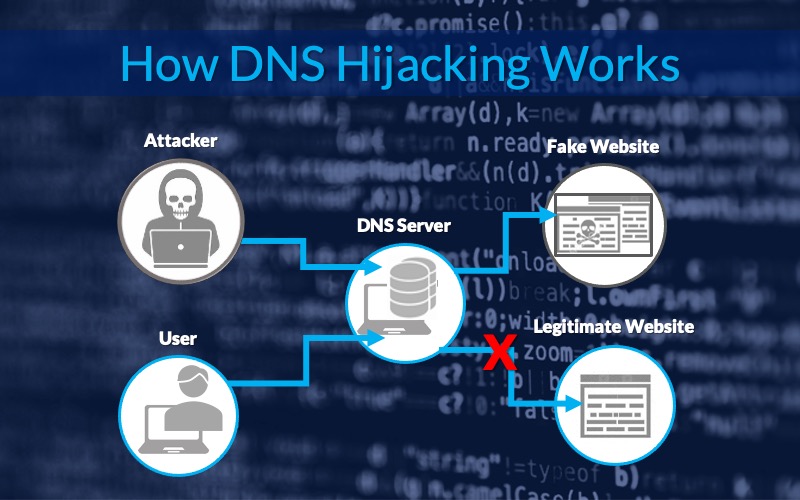
The term Domain Name System (DNS) hijacking unfortunately tends to be misused in the industry, which includes DNS poisoning for instance. In this blog post we will use the definition adopted by the UK National Cyber Security Centre (NCSC) that states “DNS hijacking refers to the unauthorised alteration of DNS entries in a zone file […]
Is your staff is staying resilient with protecting company information assets now that Working from Home (WFH) is the ‘Now Normal’? Do you know if they are aware of the tactics that threat actors are using, and do they have cyber security front of mind? If you are unsure, you are not alone. Last year, […]
Can you believe we made it through 2020? Although it was challenging, it helped us to see our strengths and showed how adaptable many of us can be. Last year helped us come closer to you, our customer, and build stronger relationships by understanding your struggles and needs. When reflecting on last year, we […]
There are a variety of different ways to assess the security integrity of the systems that process, store, or transmit your information assets. But I find it odd that this far down the cyber security road, a lot of businesses still don’t understand the basic difference between Vulnerability Scanning and Penetration Testing. I know it […]
Please be advised that SolarWinds has issued an urgent security advisory for their Orion Platform. It’s claimed that nation-state actors aggressively targeted at least two U.S. Government Agencies to include the US Department of Treasury and the National Telecommunications and Information Administration. Additionally, other global organisations in various industries ranging from telecoms, major retail chains […]
UK 2021 Data Protection Regime – Prepare & Future-Proof Compliance Welcoming 2021 with an insightful webinar, just in time to get you prepares for the upcoming years after Brexit. Time is running out for the UK to exit from the EU and we still don’t know if the UK is going to have a Data […]
A Security Engineer at Evolution Gaming has discovered a Cross-site Scripting (XSS) vulnerability on the teams.microsoft.com domain. This could be abused to trigger a Remote Code Execution (RCE) flaw in the Microsoft Teams Desktop Application. According to the researcher, an attacker simply needs to send a specially crafted message to any Teams user or channel […]
With the holiday season quickly approaching and the Pandemic tier level restrictions being unclear, many of us are turning to online shopping to purchase gifts this year. In fact, a recent Springboard survey of 1,000 shoppers reported that 61.2% plan to spend more online with only 20.4% spending at bricks and mortar stores this season. […]
ISO 27001 Certification Cost ISO 27001 is an internationally recognised standard for information security management systems (ISMS). It provides a framework for organisations to establish, implement, maintain, and continually improve their information security practices. ISO 27001 outlines clear requirements for managing risks, safeguarding sensitive information, and ensuring data confidentiality, integrity, and availability within an organisation. […]
What are the Signs of a Social Engineering Attack and How Can you Prevent Them? Social engineering is the most significant risk in the cyber threat landscape today. Over 98%[1] of cyber attacks rely on social engineering target staff as the primary attack vector, but many of you already know that. What are the signs […]