MacOS Malware “Not So Silver Linings”
Apple’s new M1 chips had no known malware for them…until now. A vulnerability dubbed the [...]
Personal Data Deletion Done the Right Way
Are you managing personal data deletion correctly under the DPA and GDPR? Does everyone in [...]
What KPIs Should be Tracked for Security Penetration Testing?
Cyber security is a journey and not just a destination. In the ever-changing security landscape, [...]
“Sharing is Caring” Unpatched ShareIT Android App Vulnerability Could Allow Hackers to Inject Malware
Several unpatched vulnerabilities were discovered in the ShareIT Android application by Trend Micro, an app [...]
“Infernal” Actively Exploited Windows Kernel EoP Bug Allows Takeover
Microsoft has secured 56 vulnerabilities in the February patch Tuesday, this includes 11 critical vulnerabilities, [...]
Did Brexit Kill the UK GDPR & Will Adequacy be Approved?
Did Brexit really kill the UK GDPR? A lot of people were confused (and rightly [...]
Ransomware Gangs are Abusing VMWare ESXi Exploits to Encrypt Virtual Hard Disks
Two CVE’s associated with VMWare ESXi are being exploited in the Wild. One major ransomware [...]
”Forged DNA”: Cisco DNA Center Bug Opens Enterprises to Remote Attack
A Cross-Site Request Forgery (CSRF) vulnerability has been discovered in the Cisco Digital Network Architecture [...]
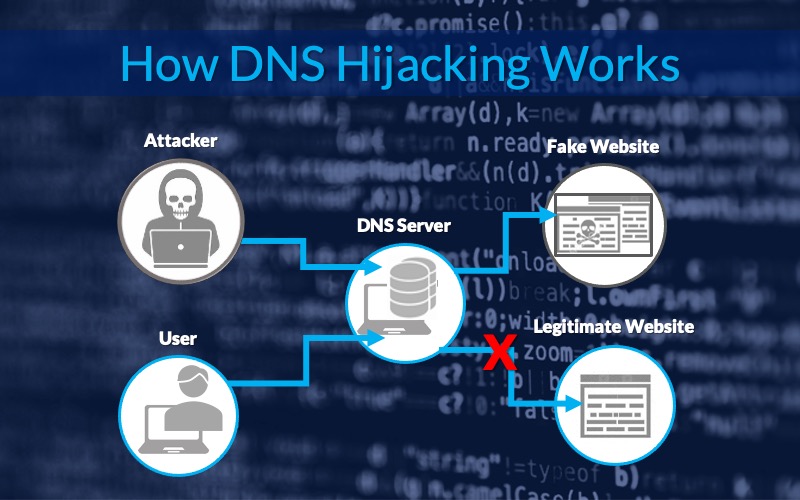
How to Mitigate DNS Hijacking
The term Domain Name System (DNS) hijacking unfortunately tends to be misused in the industry, [...]
“In Bits” IObit Forums Hacked to Spread Ransomware to its Members
The Windows utility developer IObit forums hacked over the weekend, for the threat actors to distribute [...]