Maximising Security and Efficiency with CISO-as-a-Service
Many organisations are turning to implementing a CISO-as-a-Service option. The service is not only efficient, [...]
Unlocking the Potential: Exploring the Benefits of a vCISO
There is no doubt that the number of qualified and available cyber security experts is [...]
Hiring a Virtual CISO Verses a Full Time CISO Comparison
Most of us are aware that there is a huge gap of qualified cyber security [...]
PPI Principals of GDPR for Small Businesses: Navigating Data Protection
“So, all we have to do to implement these 11 chapters containing 91 articles in [...]
3 Triggers for Conducting a DPIA
Here’s a funny thing – recital 84 of the EU’s GDPR legislation states “…where processing [...]
Personal Data Deletion Done the Right Way
Are you managing personal data deletion correctly under the DPA and GDPR? Does everyone in [...]
Data Protection Officer Questions – Answered by a DPO
There are many questions about why a Data Protection Officer (DPO) is needed and what [...]
Data Protection by Design and Default Explained
Previously known as ‘privacy by design’, “data protection by design and default” has always been [...]
When Must You Complete a Data Protection Impact Assessment?
Data protection impact assessments (DPIAs) are a legal requirement for GDPR, to ensure people’s private [...]
MOVEit Attack – Security Tool Vendors Have Failed Us… AGAIN!
2023 MOVEit Cyber Attack to Affect the Masses Yet again, here’s a prime example of [...]
Cyber Security Supply Chain Challenges in the Agrifood Sector
Guest Contributor: Benjamin Turner, Former Chief Operating Officer, Agrimetrics Shortly after Russia’s invasion of Ukraine, [...]
Supply Chain Cyber Attacks & How to Prevent Them
“There has been a 742% average annual increase in software supply chain attacks over the [...]
Cyber Supply Chain Risk Management – Should Penetration Testing be Required?
Let us begin by describing how to approach Cyber Supply Chain Risk Management (C-SCRM) and [...]
Get WFH Cyber Security at the Forefront of Staff’s Minds
Is your staff is staying resilient with protecting company information assets whilst Working from Home? [...]
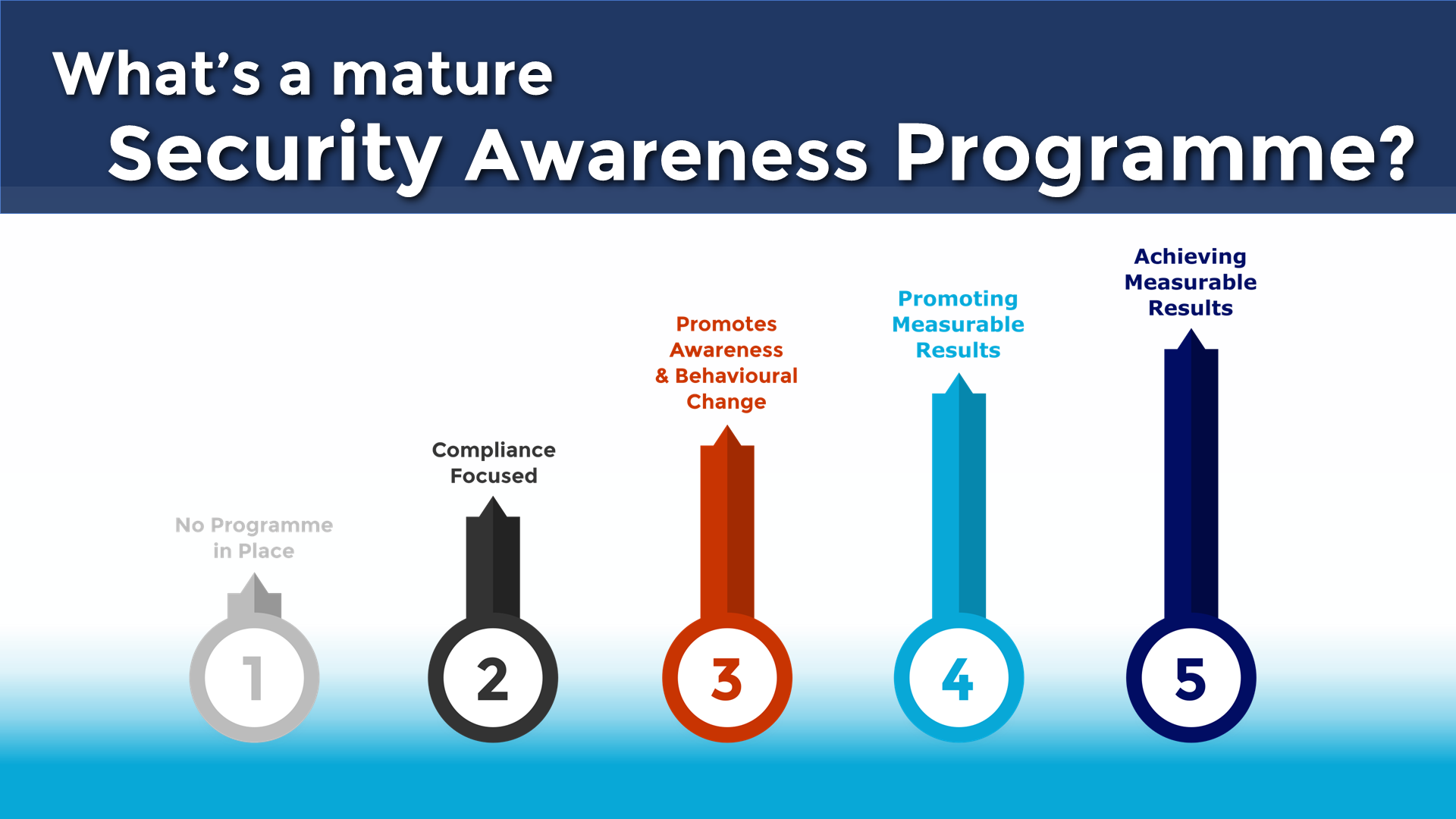
What’s a Mature Security Awareness Programme?
Good news. Bad news. The bad news is that cyber security threats to businesses are [...]
How a Ransomware Readiness Assessment Can Help Your Business Stay Safe
Ransomware is a type of malware that encrypts files and then seeks payment in exchange [...]
What is Ransomware? Four Examples You Should Know About
By now we all know the effect a Ransomware attack can have on an organisation. [...]
How to Outsmart the DarkSide Ransomware Group
The DarkSide Ransomware Group is one of the many gangs that continue to rebrand themselves [...]
Protecting Your Organisation After a Ransomware Attack
So, here is the scenario: you’re sitting at your desk working away and suddenly realise [...]
How Do You Conduct an Information Security Risk Assessment?
Information security risk assessments are crucial for any businesses that deal with any sensitive information [...]
SaaS Security 101: Essential Strategies for Businesses
Software companies have naturally embraced the cloud. It provides countless benefits for their clients, ranging [...]
As a nation, are we cyber security aware?
In the following blog post, we are going to shine a spotlight on the general [...]
How to Submit a Data Breach Breach Compensation Claim
What is a Data Breach Claim? “Someone stole my personal information and I want something [...]
How to Respond When Data Breaches Hit the Fan
Not many companies anticipate being the focal point of a significant data breach incident. However, [...]