It is estimated that six in ten SMEs that suffer a breach are likely to go out of business within six months. With COVID-19 having a huge impact on profitability this year, no business can easily recover financially from a cyber attack.
Cyber security is essential to the business’s risk management programme regardless of size. Which makes sense why businesses of all sizes make a significant investment in hiring IT talent, buying security software, and spending time on research and development for the next latest and greatest security controls.
Yet do all these investments make your business more secure? Despite significant investment, many are still suffering from cyber attacks costing thousands.
In this post, I will explain some core threats to small businesses and discuss how you can increase your resilience to cyber threats through self-awareness and planning wisely.
Be aware of the 3 common SME Hacker Attacks
It’s important that SME’s are first aware of how they may be targeted. The most common threats to be aware of include Ransomware, Social Engineering and the most critical – the Insider Threat.
1. Ransomware:
Over half of ransomware attacks target small businesses. Ransomware works by encrypting the victim’s files and displays a set of instructions, demanding payment in exchange for the decryption key, usually in the Bitcoin cryptocurrency. The ransom amount can range anywhere from a few hundred to thousands of pounds, but the impacts to business go beyond that, it can lead to a loss in reputation and trust. Worse yet, paying the ransom doesn’t always guarantee the restoration of encrypted files, or that the malware will be removed. Whilst larger businesses might be more of a lucrative target for threat actors, SME’s still make up a sizeable minority of the victims, at around 20%. In addition to this, the cost forecast of a ransomware breach is estimated to be $20 billion in total.
2. Social Engineering:
Social engineering is a collective term describing tools and techniques used to trick somebody into disclosing information, providing goods or services. The most notorious example would be a phishing email. Social engineering is so impactful because it exploits the weakest link in the security chain, the human. This is difficult to mitigate against, at least without proper training and awareness. This attack isn’t complicated either, most recently Twitter was compromised through social engineering of an employee with high privileges, which led to account takeovers of high profile celebrities and politicians, these accounts were used to initiate a cryptocurrency scam. Once an attacker has legitimate details, they can pose as a legitimate user, the more privileges the user has, the more impactful a social engineering attack can be.
3. Insider Threat:
An insider threat originates from within a business or organisation itself. A typical example is where a current or former employee with a high privileged account or access to sensitive information abuses the trust put in them. However, insider threats can also be innocent individuals who unknowingly expose information or assets to a threat actor. In fact, this is the most common scenario.
It is difficult to defend against insider threats, often because they aren’t obvious, and the motivations of each individual might be different. For example, individuals performing espionage will have different goals to that of a disgruntled employee.
4 security tips to get started with protecting your business
Although the following are not a complete list of measures to put into your risk management programme, they are a good starting place to begin strengthening your cyber resilience to attacks.
1. Become self-aware with a risk assessment:
It is important to be self-aware of your organisation by identifying what systems you use, where your staff works and what access roles they have, and if policies are in place or need to be created. A practical way to do this is to conduct a risk impact assessment. This should not only identify your systems, people and processes but provide a risk impact level to help determine what should take priority in your security programme. An assessment should be reviewed regularly to measure goals and track effectiveness.
2. Learn from your mistakes:
Incidents happen and sometimes you can’t avoid them. It is important to be able to recover and assess the information available after an incident has occurred, regardless if it was successful or not. It is important to identify potential threats to your business and assess your processes and procedures effectiveness to mitigate against them.
For example, you can conduct phishing exercises to test staff awareness, identifying individuals who are particularly at risk. Once identified you can then look at where they failed. Was it with spotting the email or failing to report the incident? When reported, did IT follow-up in a timely manner? Answering these questions will help you see if more training is required or policies and procedures need to be updated to clearly state procedures.
3. Follow the best practices:
Always have strong foundational security policies! This should take into account everything from implementing multi-factored authentication to endpoint protection. For a small business, it might not be feasible to buy cutting edge security software or have a robust information security management system like ISO 27001. But you can ensure that you are taking the minimum cyber control are in place. The NCSC has provided an informative infographic as an example, for 10 essential security practices.
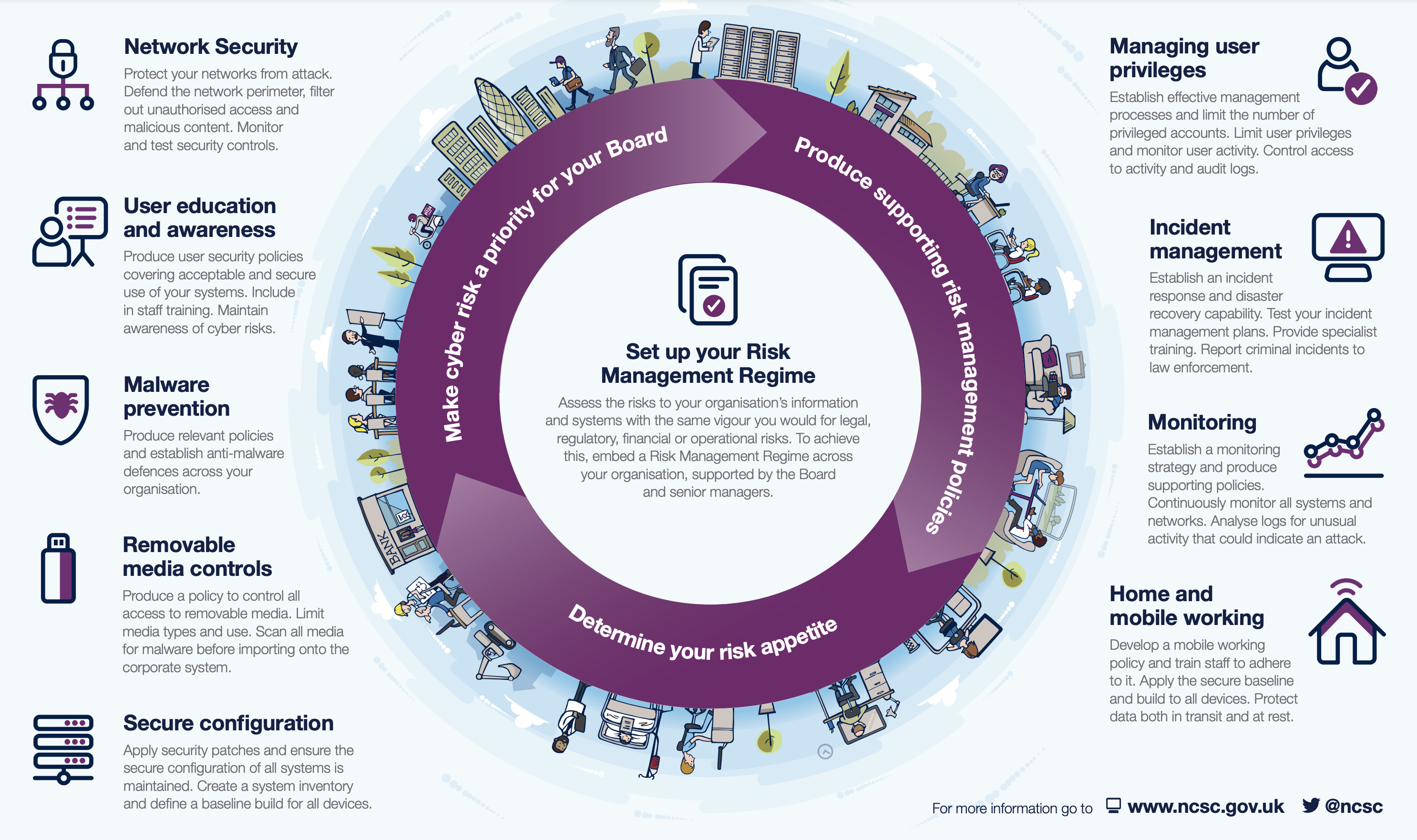
4. Invest smart:
Got a tight budget? Plan and invest smartly! By identifying threats that are specific to your business first, you can create a tailored risk management plan. This will also help you make strategic investments that are necessary rather than investing in unnecessary and expensive cyber security solutions.
By basing your security on current threats that are unique to your business, a more effective defence can be implemented, which will make an attackers life significantly more difficult. Perhaps even deterring them from pressing on with their attack. This is crucial because securing your small business could mean the difference between prosperity and decline.
Need help getting started with your risk management programme? Contact one of our security experts. They will provide you with a complimentary assessment of your current plan and advice on measures to take to advance your cyber security posture.

